This Digital Ocean VPS (Ubuntu 18.04) has up to date packages and security updates. I have 4 Simple Wordpress Sites on it which hardly gets 3-4 Thousand Visitors daily. All the sites uses authentic and up to date Themes and Plugins.
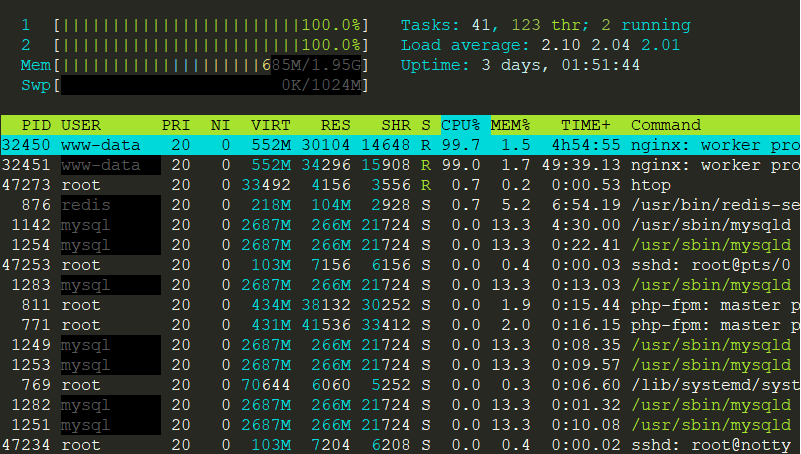
And now the Second CPU has also got 100% Usage by Nginx Worker Process with PID 32451 as shown in the following screenshot:
And here is the new log:
2018/10/31 14:31:48 [error] 32451#32451: *30900 access forbidden by rule, client: 144.76.235.84, server: ishaweb.in, request: "GET /wp-content/uploads/2018/08/seos.php HTTP/1.1", host: "www.ishaweb.in", referrer: "ishaweb.in"
2018/10/31 14:32:22 [error] 32451#32451: *30906 access forbidden by rule, client: 144.76.235.84, server: ishaweb.in, request: "GET /wp-content/uploads/2018/08/st.php HTTP/1.1", host: "www.ishaweb.in", referrer: "ishaweb.in"
2018/10/31 14:36:37 [error] 32451#32451: *30981 access forbidden by rule, client: 144.76.235.84, server: ishaweb.in, request: "GET /wp-content/uploads/2018/08/seo_script.php HTTP/1.1", host: "www.ishaweb.in", referrer: "ishaweb.in"Hello @nschopra,
looks like someone is trying to hack your wordpress sites. Do you use the latest version of wpcommon-php72.conf?
You can try to setup nginx-ultimate-bad-bot-blocker to block bad bots with Nginx, and/or configure fail2ban to ban IP after several forbidden access.
Hello Master,
These attacks are normal and I have been noticing them since a long time. Even their access is being blocked due to the rules we have used for the protections.
I have been using the latest version of WP Common PHP 7.2 and fail2ban with all the Custom Jails provided by you.
I am configuring Nginx Ultimate Bad Bot Blocker right now but I don’t think it will resolve the issue. Will keep the thread updated…
Hello @nschopra,
Okay I understand. That’s the first time I see an issue with Nginx using too much CPU.
On my servers, Nginx worker process use CPU only when there are several files downloaded from the server, and it do not use more than 15-20% of a single core.
You can try nmon to get more informations about resources usage than with htop.
apt install nmon
Thanks, Master, I will dig it more. However, I really liked Nginx Bad Bot Blocker concept but it throws the following error in the end and breaks the nginx configuration:
[emerg] "if" directive is not allowed here in /etc/nginx/bots.d/blockbots.conf:40
Tried the workarounds posted in this thread but couldn’t get it worked yet. I wish there was an article on Virtubox’s Knowledge Base about configuring this ultimate bots solution.
Hello @nschopra,
just check if directive include /etc/nginx/bots.d/blockbots.conf; was properly added in your vhost by nginx bad bot blocker script. There were few errors in 22222 and default nginx vhosts in my case.
I finally got it working but there is just one issue. As per the official thread, curl -A “Xenu Link Sleuth/1.3.8” http ://yourdomain.com or curl -I https ://yourdomain.com -e http ://zx6.ru should output the following line:
curl: (52) Empty reply from server
But in my case, there is the following output:
curl: (92) HTTP/2 stream 1 was not closed cleanly: PROTOCOL_ERROR (err 1)
It’s not an error, connection isn’t closed with the same message when you use HTTP/2.
So, I guess the setup is completed and it’s working fine. Tested it through some WP Theme Detector Sites and they were unable to access my sites.
But even after installing it there are some attempts listed in site-error log which were unsuccessful but still the Nginx CPU Memory issue is same.
Check Nginx’s changelog. It seems the issue was addressed in latest mainline.
Changes with nginx 1.15.6 06 Nov 2018
*) Security: when using HTTP/2 a client might cause excessive memory
consumption (CVE-2018-16843) and CPU usage (CVE-2018-16844).
*) Security: processing of a specially crafted mp4 file with the
ngx_http_mp4_module might result in worker process memory disclosure
(CVE-2018-16845).
*) Feature: the "proxy_socket_keepalive", "fastcgi_socket_keepalive",
"grpc_socket_keepalive", "memcached_socket_keepalive",
"scgi_socket_keepalive", and "uwsgi_socket_keepalive" directives.
*) Bugfix: if nginx was built with OpenSSL 1.1.0 and used with OpenSSL
1.1.1, the TLS 1.3 protocol was always enabled.
*) Bugfix: working with gRPC backends might result in excessive memory
consumption.Yes, I even I saw the same changelog yesterday and also updated to the latest one (Thanks to @virtubox 's Nginx EE Scripts) but still, the issue is same. Nothing is changed for me as of now 
It didn’t solve my problems neither. 
Hello, do you have any news regarding this topic?
I just started using Ubuntu 18.04 (almost 200 VPSs and dedicated servers to move). There are no errors with “stock” Nginx (the one from repositories), but it is 14.0, not even up to date with stable release.
And I’m afraid of compiling Nginx again and getting the same issue from the other servers.
Any opinion would help.
Thanks in advance.
I can’t tell if it’s the solution for this mystery or not, but I’ve got some good results by removing (commenting) the line aio threads in nginx.conf.

It’s not aio thread the cause of the issue.
Now I commented brotli on; for a new test (Brotli and AIO Threads are disabled).
So far, so good. I think it’s Brotli to blame for the CPU hogging.
Hey @portofacil Thanks a lot of keeping the thread updated and giving the suggestions. As I am not a server expert so it’s really hard for me to use the official Nginx and remove the existing one.
However, I will surely try removing brotli and Aio threads lines from nginx.conf and see if it works. I will let you know the outcome in my case.
Thanks 
It’s like a dream: 24h and no issues with Nginx in any of my servers!